As cybercriminals grow more sophisticated, universities are facing a new wave of phishing attacks that are harder to detect and more damaging than ever before.
New York University, Columbia University and now the University of Pennsylvania have all experienced massive data breaches in the past year.
Late last week, a group of hackers purportedly accessed over 1.2 million lines of data at Penn. While university officials have yet to verify the exact number, thousands of pages of internal documents have already been released, including confidential correspondence among staff, bank transactions and personal identifying information, according to the university’s independent newspaper.
Hackers accessed Penn’s system with stolen credentials, which they may have gained from students and alumni by sending emails impersonating university officials, the university said in a statement.
“Even the most sophisticated security systems are vulnerable to social engineering attacks—when bad actors deceive individuals into giving up confidential information, which compromises security and can be used to access private systems and information.”
How phishing is evolving in higher education
Artificial intelligence has dramatically improved the tools and techniques of scammers, including the age-old method of phishing.
“What once were easily spotted scams—riddled with spelling mistakes, awkward phrasing, and generic greetings—are now sophisticated, AI-generated messages that closely mimic legitimate communication,” said James Turgal, vice president of global cyber risk and board relations at Optiv.
Beyond correcting obvious grammar mistakes, what makes generative AI even more dangerous is that it can mimic the writing style and tone of a trusted organization.
More on cybersecurity: 5 data privacy and security resolutions for universities in 2025
Higher education is a prime target for social engineering attacks, Turgal explains. Colleges and universities—housing intellectual property and vast amounts of personal data—lack consistent security. Thousands of students join or depart campus systems each year, creating a dynamic but porous digital landscape.
A single student or donor who is unaware of social engineering can be robbed of their credentials and become a massive liability to a college’s cybersecurity framework.
Beating back the wave of data breaches
Higher education leaders must educate their community about the subtle clues that can still expose a malicious email, Turgal advises. For example:
- Slight variations in domain names or “lookalike” domains that resemble official ones.
- Language that creates urgency or fear, such as threats of account suspension or financial consequences.
- Unsolicited attachments or unexpected links, particularly those prompting credential entry.
- Shortened or obfuscated URLs that conceal the true destination.
- Requests for sensitive information. Legitimate organizations rarely, if ever, ask for passwords or payment details via email.
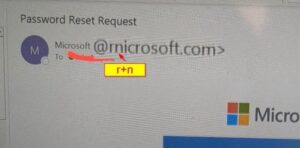
Staff, students and donors must pause to verify an email with the line between fraudulent and authentic getting blurrier every day. Universities should provide ongoing cybersecurity training to keep users vigilant.
“Just as institutions routinely conduct fire or weather drills, they should regularly practice cyber hygiene to ensure preparedness and awareness across the campus community,” Turgal says. “It must become an integral part of the university’s culture.”
Additionally, universities must educate users on how to report potential phishing attempts to the IT team. This can be streamlined by integrating an easily accessible “Report Phishing” button or a direct hyperlink within the email platform.
“Ultimately, technology alone cannot protect an organization. By cultivating a culture of shared cybersecurity responsibility, supported by continuous education and transparent communication, universities can dramatically reduce their risk of becoming the next target.”